Built to inform decisions and action for modern security operations... Mallory enables CTI, SOC, Detection Engineering,
Exposure Management, and GRC teams.
EPSS
- Percentile72%
- Probability41%
- CVSS V3.19.8
- Attack VectorNETWORK
- Attack Complexitylow
- Privileges RequiredNone
- User InteractionNone
- ScopeUNCHANGED
- Confidentiality Impacthigh
- Integrity Impacthigh
- Availability Impacthigh
- Base Score9.8
- Availability ImpactCRITICAL
- Base Score0
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Tactic
Techniques
References
Resource Development
1
2 Sources
Initial Access
1
2 Sources
Discovery
1
2 Sources
Defense Evasion
1
2 Sources
Execution
1
2 Sources
Primary target sectors
- Healthcare20%
- Manufacturing15%
- Public/Government14%
- Financial Services11%
- Food and Supply Chain9%
8 updates in the last year
2024
All
Many Malware Campaigns Linked to Proton66 Network
The king thought long and hard, and finally came up with a brilliant plan: he would tax the jokes in the kingdom.
- peerspot.com/categories/cis…
- cert.europa.eu/publications/security-advisories/2025-021
- www.scworld.com
- www.techradar.com/news/cybersecurity
- www.infosecurity-magazine.com/news/new-cybersecurity-trends-2025
- www.securityweek.com/articles/2025-cyber-threats
- www.krebssecurity.com/2025-data-breach-reports
Mallory is built for proactive security teams to understand, prioritize, and act on the threats that matter most to their organization.
DOMAIN
SPECIFIC LLM
SPECIFIC LLM
DATA CORRELATION
& ENRICHMENT
& ENRICHMENT
SUBSCRIPTIONS
& INTELLIGENT AUTOMATION
& INTELLIGENT AUTOMATION
AGENTIC ANALYSIS
& RESEARCH
& RESEARCH
OSINT
Dark Web
Commercial Intel
Threat Profile
Tech Profile
Org Context
Correlate and Contextualize your Intelligence Universe
Mallory automatically correlates vulnerabilities, indicators, threat actors, and real-world events adding technical, historical, and organizational context so analysts can make decisions without manual enrichment.
Customize Mallory to Your Security Workflows
Configure intelligent, context-aware notifications that align with your existing processes so teams can act immediately when a relevant threat emerges.
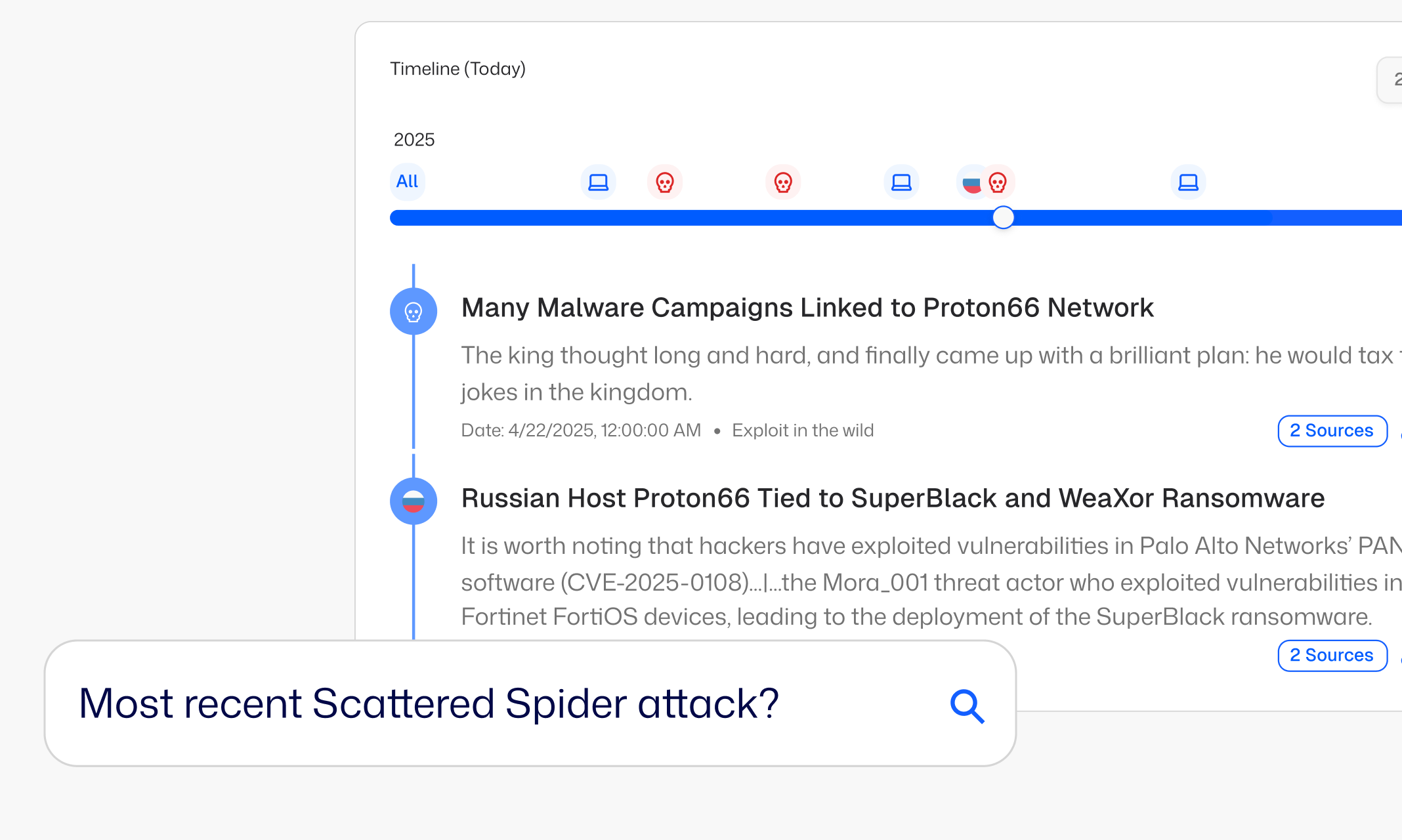
Search Contextualized Real-Time Intelligence
Always-on collection enables continuous research and organization of intelligence aligned to your Priority Intelligence Requirements (PIRs).
Improve MTTD
Detect and prioritize relevant IOCs faster by focusing on threats aligned to your environment and risk profile.
Scale Response
Analyze attacker TTPs and emerging attack patterns that require proactive hunting and discovery.
Enable Remediation
Rapidly determine exposure and impact so remediation can begin in minutes - not hours or days.
Ensure Compliance
Map security actions directly to compliance requirements and demonstrate measurable risk reduction.
Early Access
Ready to Supercharge your Security Operations?
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
